Reduce risk by shining a light on shadow apps
Secure your environment and get control of SaaS sprawl with shadow app detection, monitoring, and management.
Trusted by IT and Security @










By 2027, 75% of employees will be accessing tech outside of IT's view
*Gartner
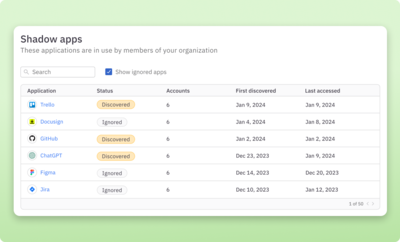
Close your SaaS visibility gaps
Immediately identify and catalog shadow app usage for a comprehensive, real-time view into all cloud access.
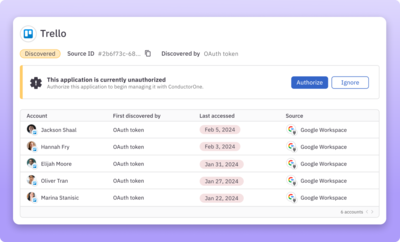
Understand how shadow apps are being used
Track all login activity for known shadow apps to determine whether to bring them under management.
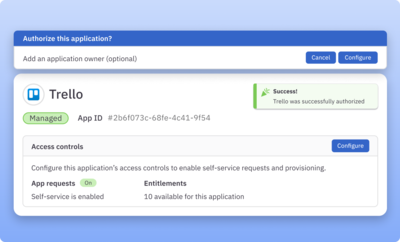
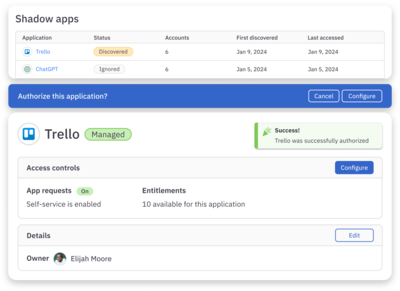
Sanction and secure shadow apps in a few clicks
Simply authorize shadow apps to bring them under management and enforce access controls. Ignore shadow apps that are of low concern—they can be un-ignored at any time.
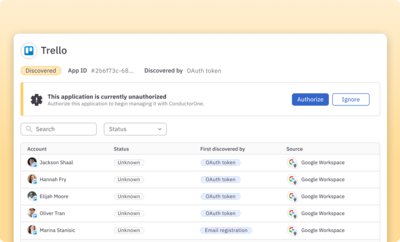
Reduce the risks of OAuth-enabled shadow apps
Ensure OAuth-enabled accounts are immediately discovered and brought under management.
Eliminate unnecessary SaaS spend
Lower your overall SaaS costs by bringing shadow apps under management. Eliminate unnecessary apps, control access, and monitor ongoing usage.
“Surfacing unauthorized and unmanaged applications was a missing component in our overall visibility. Being able to not only identify these applications but incorporate them into our access controls workflow is solving a big pain point for us.”

Emanuel Francisco
TechOps Team Lead

Features
App detection
Identify and catalog new shadow app account activity in real time.
Usage monitoring
Track additional sign-ups and usage frequency.
Option to manage
Opt to authorize shadow apps in ConductorOne for full access control capabilities.
Option to ignore
Opt to ignore lower-concern apps. Un-ignore at any time to see and manage usage.
Access controls
Configure robust access controls for managed apps to enforce security and optimize license usage.
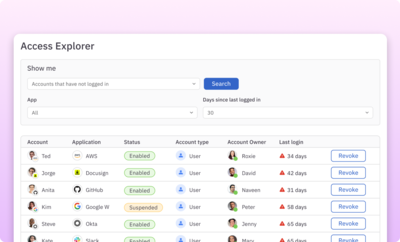
Access fabric
Get real-time visibility into unused and orphaned accounts to proactively secure access and manage costs.
Introducing Baton Feeds
Learn how the latest update to Baton, our open-source connector interface, powers shadow app detection.