Guides




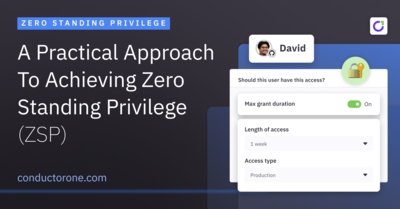
A Practical Approach to Achieving Zero Standing Privilege (ZSP)
ZSP is a core tenant of a Zero Trust approach to cybersecurity, and implementing it has knock-on benefits beyond improved security. This guide looks at the current security landscape to understand why ZSP is an effective solution for protecting hybrid and cloud-first environments and provides a tactical approach to achieving ZSP.



Everything You Wanted to Know about GitHub Access Control
GitHub, the largest and most popular software development platform, providing services from Git version control to bug tracking, CI/CD, and task management which makes it an extensive system to manage access controls. This article explores everything you need to know about GitHub access control to properly manage your accounts and repositories on all levels.


Snowflake Authorization and Permission Model Deep Dive
Snowflake's robust authorization and permission model is central to how a company secures data in the platform. This comprehensive guide dives deep into the entities and methodologies that comprise Snowflake's permission model and its relative strengths and limitations.

Securing Identity for Any Application: Deep Dive into ConductorOne Integrations
Digital transformation and cloud applications are rapidly reshaping the tech landscape, however many businesses still operate in hybrid application environments. This guide dives into the different kinds of environments seen across companies, reasons for adopting a hybrid architecture, and ConductorOne’s integration support for any type of architecture.


Stay in touch
The best way to keep up with identity security tips, guides, and industry best practices.