Just-in-time access is based on the principle of the least privilege, which is a security concept that restricts user access rights to the bare minimum necessary to perform their job functions. This is done by allocating access rights based on specific requests and automatically revoking them after a set period or task completion.
What Is Just-in-Time Access (JIT)?
Just-in-time (JIT) access is a security model and access management practice that grants users access to applications or systems on an as-needed basis for a set period of time. This helps to minimize over-permission, standing privileges, and other provisioning risks by ensuring that only the necessary level of access is granted to a user.
Furthermore, implementing JIT involves a combination of identity and access management (IAM) solutions, privileged access management (PAM) tools, and often, custom automation workflows. These systems work together to authenticate users, evaluate access requests against predefined policies, and provision access rights in real time.
Unlike traditional access management models that might grant users permanent or extended access privileges, JIT ensures that access is granted on a strictly necessary basis, thereby minimizing potential security risks associated with overly broad or persistent access rights.
How Does JIT Access Work?
💡The JIT access mechanism requires a robust system to manage access requests, approval processes, and the automatic provisioning and deprovisioning of access rights. Here’s how they all work together:
- Request for Access. The process begins when a user requests temporary access to a resource. This request typically includes the reason for access, the specific resources needed, and the duration of access.
- Authentication and Authorization. The system authenticates the user to verify their identity and then checks if the user is authorized to request access to the specified resource. This step might involve integrating with an Identity Provider (IdP) or using an Identity Access Management (IAM) system.
- Approval Workflow. For sensitive resources, the request may be routed through an approval workflow. This workflow can involve one or more approvers, who review the access request based on predefined policies, the risk level of the access, and the context of the request (e.g., time of day, user’s role).
- Dynamic Access Provisioning. Once the request is approved, the system dynamically provisions access to the resource. This provisioning is tailored to the request’s scope, granting only the permissions necessary for the task.
💡Tip → Dynamic access provision is the automated process of granting, revoking and adjusting user access rights to resources in real-time, based on predefined policies.
- Monitoring and Auditing. Throughout the access period, the system monitors user activities to ensure compliance with policies and to record operations for auditing purposes. This step is crucial for maintaining security and for forensic analysis in case of incidents.
- Automatic Access Revocation. After the approved duration expires, the system automatically revokes the access. This ensures that the permissions do not remain active beyond the necessary timeframe, thereby reducing the risk of misuse or attack.
Related → User Access Reviews: Process & Best Practices Checklist
Types of Just-in-Time Access
Justification-Based Access
Justification-based access is a subcategory of JIT access that requires users to provide a valid reason or “justification” for privileged access.
Once approved, users gain limited access to resources for a set period of time. The credentials for these accounts are managed and rotated in a centralized vault, and users are not made aware of them after using them to reduce the risk of access privilege abuse.
How Justification-Based Access Works
The requestor submits an access request and a justification for why the access is needed.
The access control system evaluates the justification against the organization’s policies and the current context (e.g., time of day, requestor’s role).
The policy engine decides whether the justification is sufficient for granting temporary access. This decision may involve manual approval from a human supervisor or be fully automated.
If the request is approved, access is temporarily granted to the requestor. The scope and duration of this access are strictly controlled and often automatically revoked after a predefined time or upon completion of the task.
💡Practical Application
Say a member of your team needs to access a secure computer system for a task like fixing a bug or updating software. They’ll have to put in a request explaining why they need access and for how long.
Then, the IT department checks this request, agrees, and gives them a temporary password. This password works only for a short time, just enough to do the job. After that, the password stops working, which helps prevent unauthorized people from getting into the system later on.
Ephemeral Accounts
Ephemeral accounts are created for one-time use only. They are specifically tailored to facilitate users—often third-party contractors, vendors, or temporary employees—in completing a distinct task or project within a predetermined time frame.
Once the user’s need for access concludes, the access period expires, and the account is promptly disabled and subsequently deleted from the system.
How Ephemeral Accounts Work
- A user or system requests access to a resource, specifying the need and duration of access.
- Based on the request and adherence to policy, an ephemeral account is dynamically generated with specific access rights.
- The requestor uses the ephemeral account to perform the necessary tasks within the access period.
- After the task is completed or the expiration time has passed, the account automatically expires. Access is revoked, and the account is deleted.
💡Practical Application
When a company hires a contractor for a short project, like upgrading the website, they create a special, one-time account for the contractor to use. This account lets the contractor access only what they need to do the job.
Once the project is finished, the company deactivates and removes the account. This prevents the contractor from accessing the system, keeping the company’s information safe.
Temporary/Privilege Elevation
This JIT access control mechanism focuses on granting elevated access rights to users for a limited period. This approach allows users to perform specific high-level tasks or address urgent issues that require broader access than their normal privileges would permit.
When the task is completed or the time expires, the elevated privileges are automatically revoked, reverting the user to their standard access level.
How Temporary/Privilege Elevation Works
- A user requests elevated access, providing a justification for the elevation.
- The request is evaluated based on predefined policies, which may involve automated checks or manual approval from a higher authority.
- Once approved, the user’s privileges are temporarily elevated, granting them the access necessary to complete the task.
- After the task is completed or the designated time expires, the elevated privileges are automatically revoked.
Related → What is Temporary Elevated Access?
💡Practical Application
When a company employee needs extra permissions to do a specific job, like updating system settings, they can ask for temporary higher access. This special access lets them do the task that they normally can’t. Once they’re done or after a set time, this extra access is taken away. This ensures that employees only have the extra powers when needed, keeping the system secure.
Benefits of Just-in-Time Access
Enforces Least Privilege Access
JIT access works on the principle of “least privilege access” — i.e., ensuring users receive only the necessary permissions for a limited time. This strategy reduces unauthorized access risks and minimizes the attack surface by dynamically adjusting access rights based on immediate needs.
With this security model, JIT minimizes the opportunities for attackers to exploit unused or excessive permissions by keeping the overall number of privileged accounts to a minimum.
To make all of this possible, JIT implements identity and access management (IAM) systems, privileged access management (PAM) solutions, and real-time monitoring.
- IAM systems to manage user identities and enforce access policies.
- PAM solutions to control and monitor privileged account use — which is critical for security.
- Real-time monitoring to detect unusual access patterns, facilitating quick responses to threats.
Related → Best Practices for Privilege Access Management for the Cloud
Reduces External Threat Exposure
The tightly controlled time frame and “access-as-needed-basis” on which JIT access operates reduces the risk of external attackers exploiting users’ credentials.
In addition to this, the dynamic nature of JIT access means that permissions are constantly evaluated and adjusted based on real-time needs, thereby minimizing the window of opportunity for unauthorized access or attacks.
Reduces Internal Risk Exposure
Insider threats are often the hardest to detect because the employee perpetrating the act knows all the security protocols.
A typical example was the case of a General Electric employee who stole more than 8,000 sensitive files over the course of eight years in an attempt to start a rival company [*]
Incidents like this necessitate the need for JIT access as it reduces the potential for internal users to misuse or mishandle sensitive information. This is solely possible because their access is restricted to periods when it is explicitly required for their job functions.
Additionally, JIT access enhances the security posture of an organization by providing detailed logs and monitoring capabilities that track when, why, and for how long access is granted. This level of auditing is useful for detecting unusual access patterns or behaviors that could indicate a security risk or policy violation.
💡Pro Tip → With ConductorOne’s access fabric, every access request and approval through JIT is logged, creating an audit trail that provides visibility into who accessed what, when, and why. This supports compliance and security monitoring by ensuring that all actions are attributable and that any misuse can be quickly identified and addressed.
Reduces Administrative Burden and Saves Valuable Time
Traditional access management systems often require manual intervention to grant, adjust, or revoke user permissions, a process that can be both time-consuming and prone to error.
JIT access automates these procedures, allowing for dynamic allocation of access rights based on set policies and real-time user requests. This automation streamlines the process of access management, cutting down the time IT staff spend on routine tasks, such as setting up user accounts or adjusting permissions in response to role changes.
This reduced need for manual oversight accelerates operations and minimizes the risk of human error. It also ensures that access rights are accurately aligned with organizational policies and user requirements.
Related → Why Migrate from Birthright to Just-in-Time (JIT) Access?
Streamlines Compliance and Audit Processes
If your organization is regulated by stringent compliance standards, maintaining detailed records of who has access to what, when, and for how long is critical.
By implementing JIT access, you can easily automate the logging of all access-related activities, thereby, providing a comprehensive audit trail that simplifies the review and analysis process for compliance purposes. This level of detail demonstrates your organization’s adherence to various regulatory requirements, such as GDPR, HIPAA, or SOX — all of which mandate strict control and oversight of access to sensitive information.
Related → SOX Access Controls, Separation of Duties, and Best Practices
How to Implement Just-in-Time Access in Your Organization
Define Access Requirements
- Begin with creating a comprehensive inventory of roles within your organization. This includes job titles and the functions associated with each role. Understand that roles are different from individuals; a role represents a set of permissions required to perform specific job functions.
- Determine which roles in your organization require access to specific resources, such as applications, systems, databases, or other critical infrastructure components.
- Define the access levels needed for each role. Consider read-only, write, or administrative privileges based on the principle of least privilege (PoLP).
- Read-Only Access. Allows users to view or read data without the ability to modify it. Suitable for roles that require monitoring or auditing functions.
- Write Access. Grants the ability to modify, add, or delete data. This level is necessary for operational roles involved in data entry, updates, or development tasks.
- Administrative Access. Provides full control over systems and applications, including the ability to change configurations, manage user accounts, and install software. This is typically restricted to IT support roles.
💡For highly sensitive roles or resources, consider implementing time-bound access, where permissions are only active during certain hours or under specific conditions. This limits the window of opportunity for potential misuse.
Related → A Practical Approach to Achieving Zero Standing Privilege (ZSP)
Evaluate Current Access Management Solutions
- Assess your current (IAM) solutions to determine if they support JIT access. This includes built-in capabilities for JIT access and options for third-party integration that enable JIT provisioning of access rights.
- Identify any gaps in your current system that might hinder the implementation of JIT access. This could involve the need for additional features or integration capabilities with other security solutions.
- Evaluate the system’s load-handling ability — especially for a significant number of access requests during peak times. JIT access systems must be scalable and performant not to introduce latency into the access provisioning process.
💡Examine the existing authentication methods (e.g., passwords, biometrics, tokens) and authorization processes to ensure they are robust and can support dynamic access controls.
Choose the Right JIT Access Solution
Identify and document specific use cases within your organization that require JIT access. This could range from contractors needing temporary access to certain systems, to employees requiring occasional access to sensitive data. Key features to look for include:
- Ease of use
- Scalability
- Support for multifactor authentication (MFA)
- Automated workflows
- Comprehensive reporting and auditing capabilities.
Evaluate vendors based on security features, compliance standards (e.g., GDPR, HIPAA, SOX), Service Level Agreements, customer support, total cost of ownership (TCO), and cost.
💡Before finalizing your decision, conduct a pilot test of the JIT solution within your environment. This helps ensure compatibility, assess the ease of implementation, and evaluate the solution’s impact on your operational workflows.
Integrate JIT Access with Identity Providers (IdPs)
- Integrate the JIT solution with your organization’s identity providers (IdPs). This integration is crucial for automating the authentication and authorization process.
- Here’s how it works:
- When a user requests access to a resource, the JIT system redirects the user to the IdP for authentication. Upon successful authentication, the IdP returns an authentication token to the JIT system, which then grants or denies access based on predefined policies.
- Here’s how it works:
Related → What is the Difference Between Identity Governance and SaaS Security Posture Management?
Automate Access Provisioning and Deprovisioning
- Design automated workflows that guide the access request through approval processes, provisioning, and eventual deprovisioning. These workflows should be designed to minimize manual intervention while ensuring compliance with organizational policies.
- Implement self-service portals that enable users to request access as needed. These requests should trigger automated workflows that assess them against established policies and either grant access directly or route them to the appropriate approver.
- Set up automated triggers for deprovisioning access. These include the expiration of the access period and triggers based on changes in employment status, role changes, or the completion of specific projects.
- Automate regular access reviews to ensure that access rights remain aligned with current needs and policies. This can include automated reports for managers or IT administrators to review and confirm or adjust access rights as necessary.
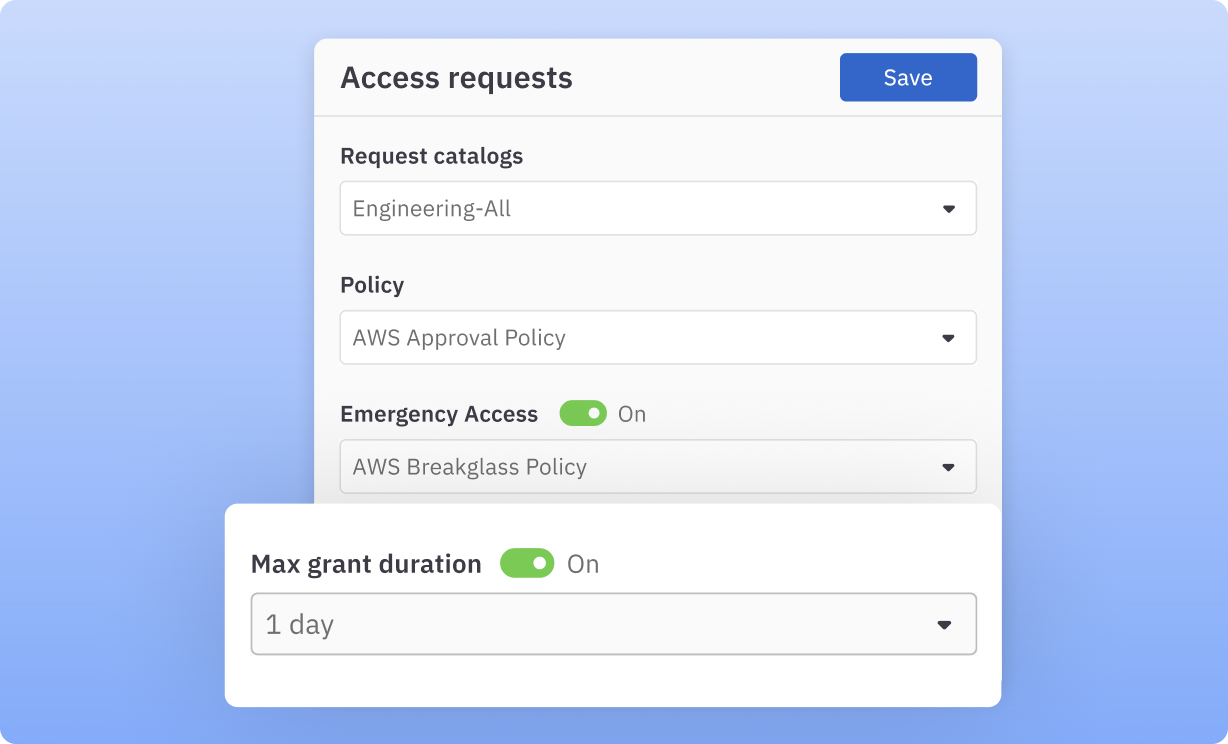
💡Establish conditions under which access is granted. This might include factors such as the time of day, location, device security posture, and specific project requirements. Also, define the maximum duration for which access can be granted. Access should automatically expire at the end of this period unless explicitly renewed.
Monitor and Audit Access
- For comprehensive coverage, choose tools that can monitor access across all platforms and resources, including cloud services, on-premises servers, applications, and databases.
- Ensure that these tools integrate seamlessly with your existing security infrastructure, such as SIEM systems, to enable centralized monitoring.
- Track login attempts, access requests, actual accesses, and any modifications made to data or configurations.
Also, monitor the context of access, including time, location, device used, and network security posture, to identify potential security risks.
💡Protect audit logs from unauthorized access and tampering. To do this, you can utilize write-once-read-many (WORM) storage for encryption or ensure the logs are stored in a secure, tamper-proof environment.
Train Employees
- Develop training content that is relevant to your organization’s specific use of JIT access. Include scenarios that employees are likely to encounter in their day-to-day work.
- You can use a mix of training formats, such as e-learning modules, webinars, and live workshops, to cater to different learning styles. Gamification and interactive elements can also increase engagement.
- For IT staff and security teams, provide detailed training on the configuration, management, and monitoring of the JIT access system. This includes setting up roles, defining access policies, and integrating with existing IT infrastructure.
They should also have the skills to troubleshoot common issues that may arise with JIT access, including authentication problems, access delays, and integration errors.
Secure Your Sensitive Resources With ConductorOne
ConductorOne’s just-in-time (JIT) access is designed to enhance security and efficiency by providing temporary, time-bound access to resources when needed.
With ConductorOne you can:
- Protect cloud infrastructure and data. Out-of-the-box integrations enable unified just-in-time access to AWS, GCP, Snowflake, GitHub, and many more.

- Automatically provision temporary elevated access. Grant temporary elevated access with automatic time-bound provisioning and deprovisioning.
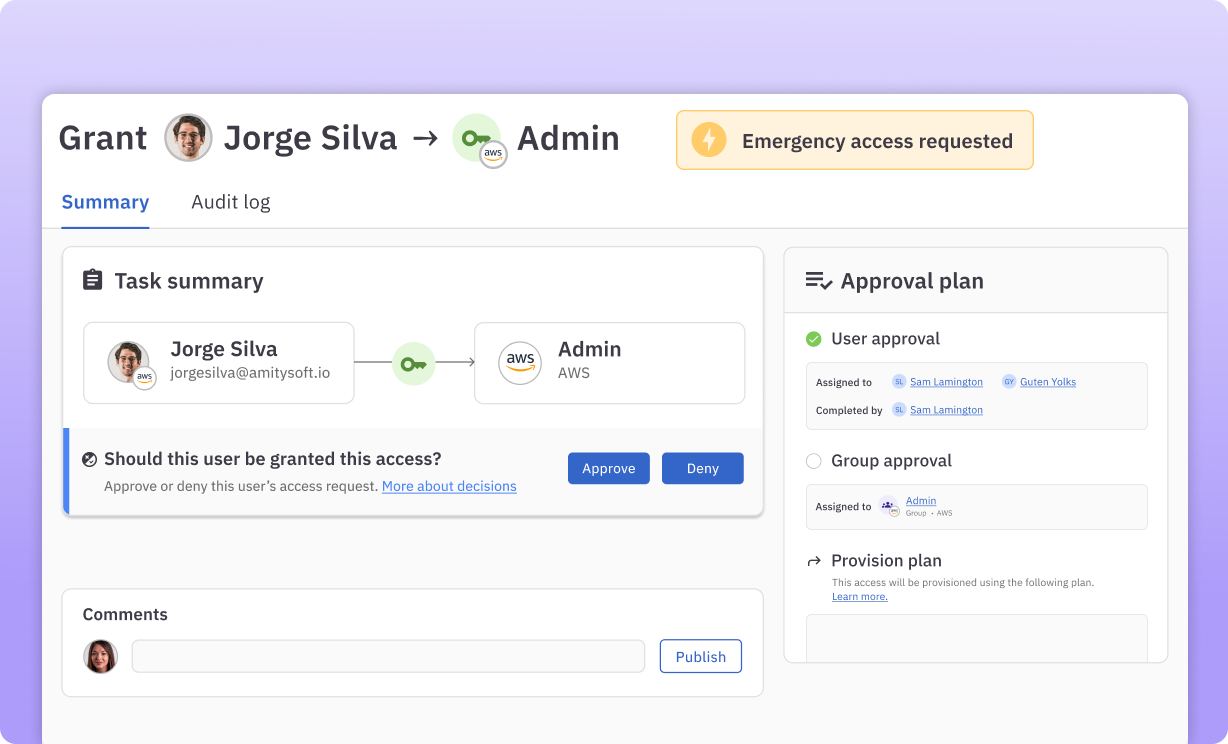
- Provide break-glass access for sensitive permissions. Escalate time-bound sensitive access requests with a different approval policy.
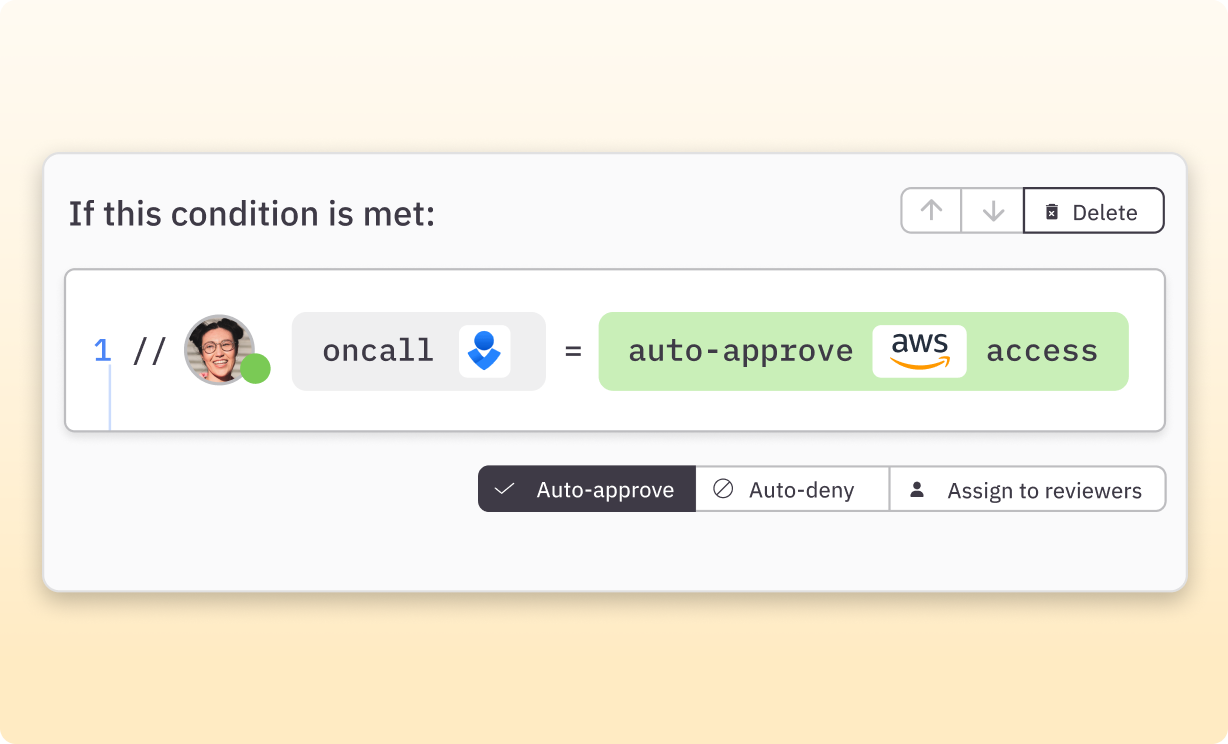
- Auto-approve JIT access for on-call users. Use conditional policies to automatically approve JIT access for on-call rotations.
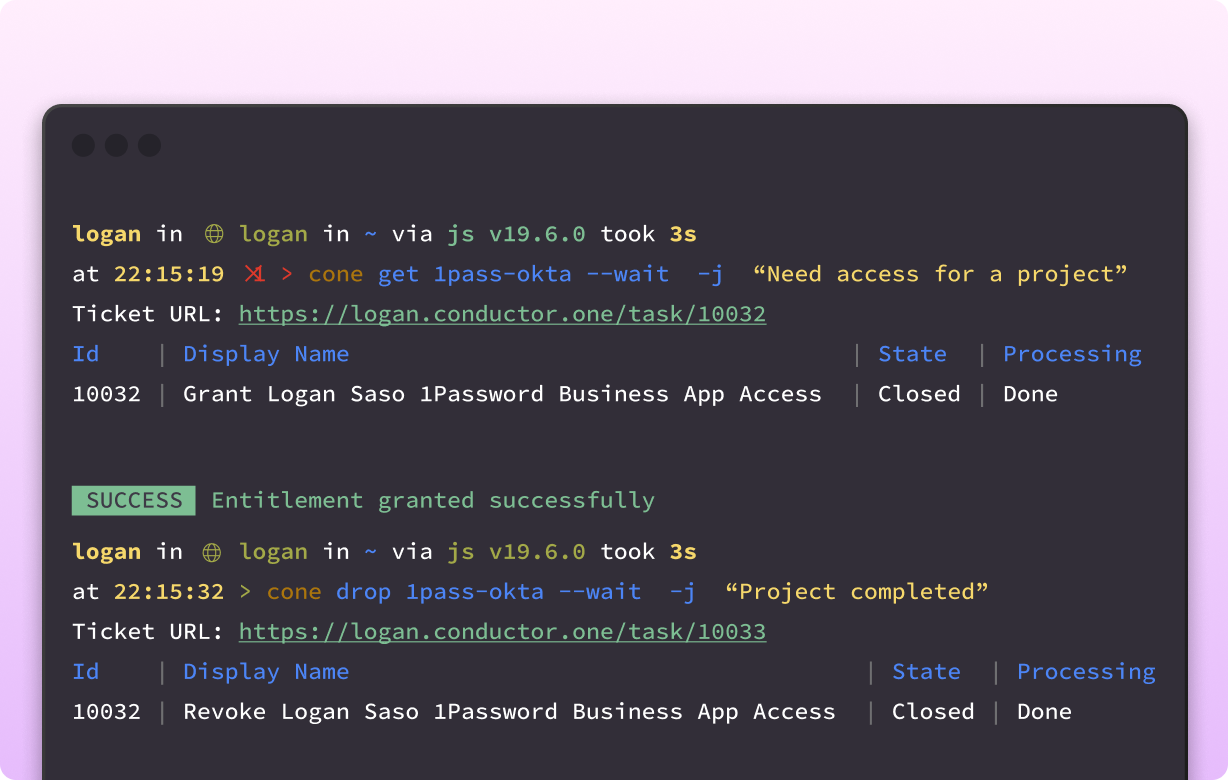
- Leverage a developer-friendly command line interface (CLI). Use the ConductorOne CLI (Cone) to search the app directory, escalate permissions, and request or approve access.
- Apply JIT access to any role, resource, or permission. Create JIT access policies for fine-grained permissions, roles, groups, or resources.
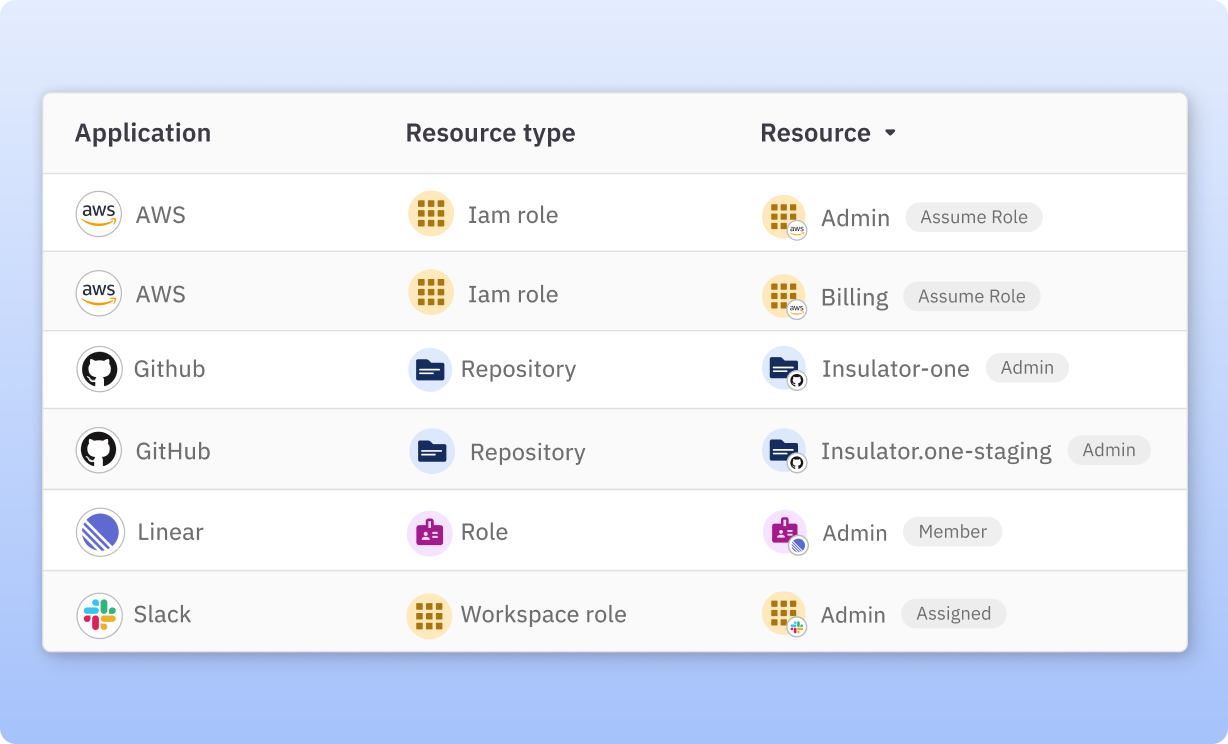
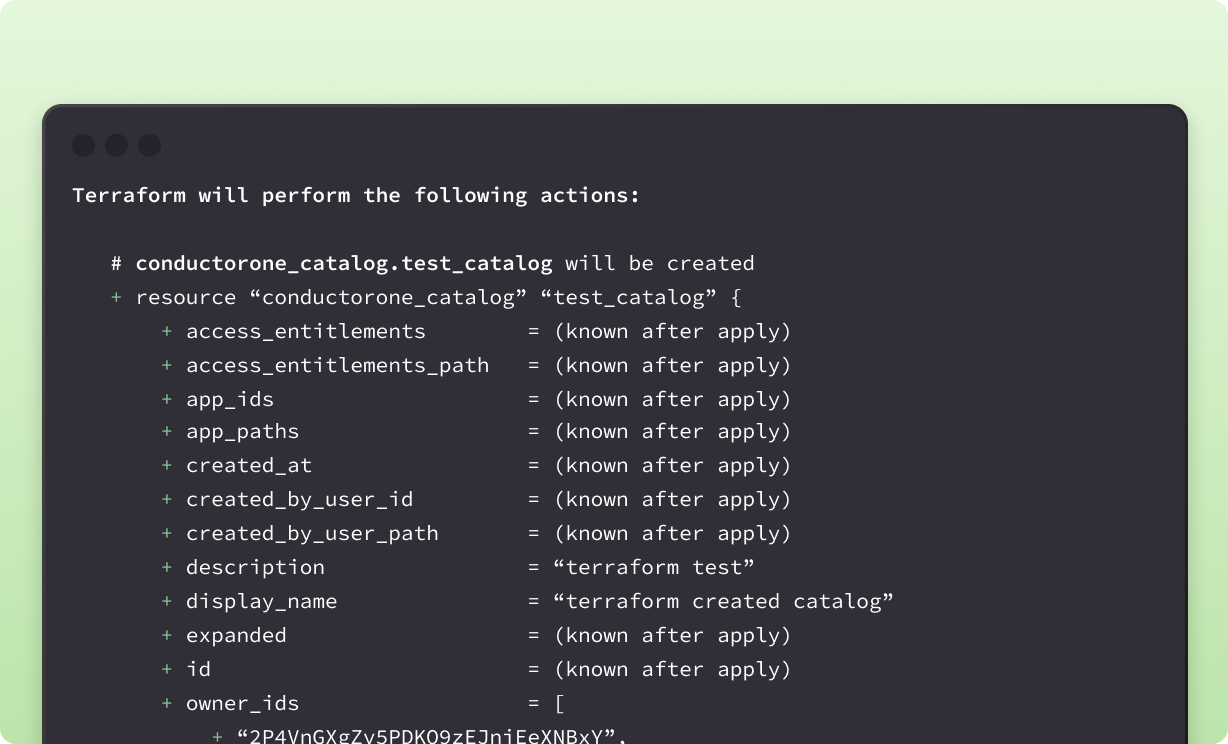
- Configure JIT policies with Terraform. Define access controls “as code” with Terraform and apply JIT policies to your apps and infrastructure.
- Track all access from one control plane. Audit all access changes, approvals, grants, and remediation activity in one place.
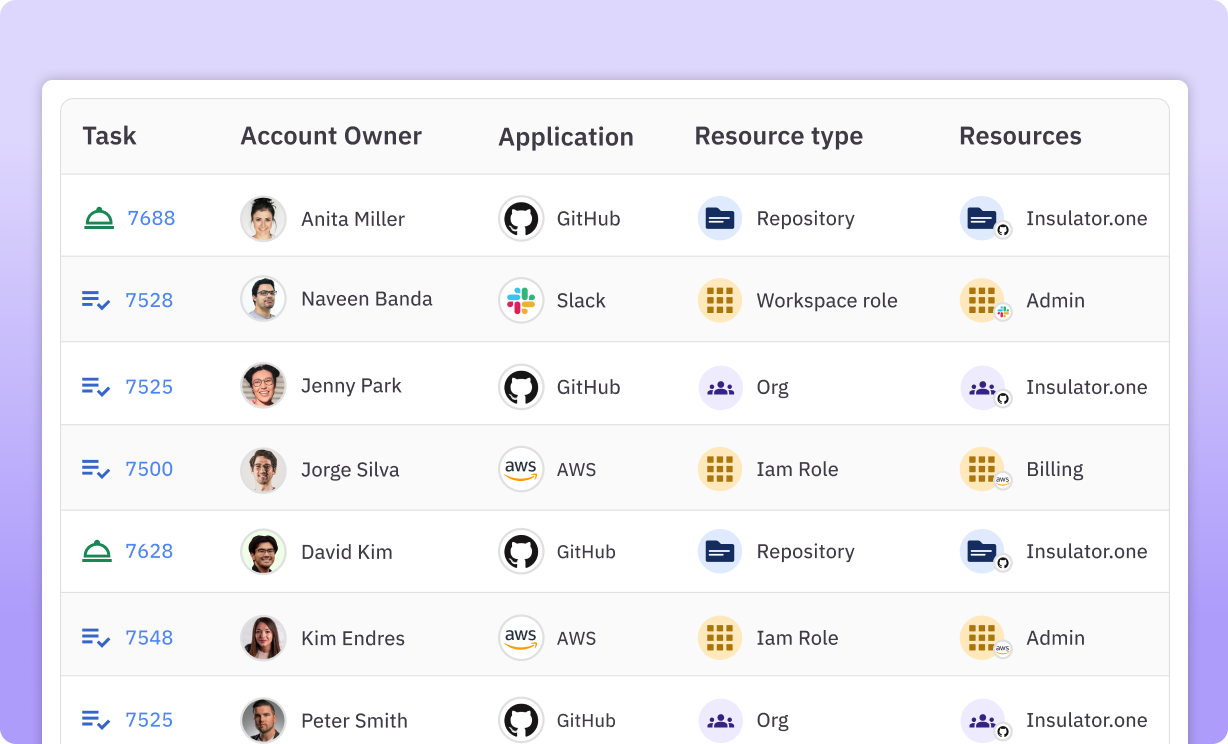
💡Case Study → How Ramp Implemented Least Privilege Access
- Automated quarterly user access review campaigns for SOC 2, ISO 27001, and PCI DSS.
- 95% reduction in IT effort required to process access request tickets.
- One place to view and audit access continuously across Ramp’s systems and enforce least privilege access controls.
Just-in-Time Access FAQs
What is the difference between just-in-time access and zero trust?
Just-in-time access is a control mechanism that provides temporary access, while zero trust is a broader security model that requires verification of every request as if it originates from an open network. JIT can be a component of a zero trust strategy by ensuring access is only granted when needed and justified.
How does JIT improve cybersecurity compared to traditional access controls?
JIT reduces the risk of unauthorized access and potential internal or external threats by limiting the access window to what is necessary for the task, reducing the attack surface.
What are the benefits of using JIT access in a PAM solution?
In a PAM (Privileged Access Management) solution, JIT access minimizes the risk of privileged credential abuse by granting temporary privileges, enhancing security, and ensuring compliance with the least privilege principle.
How does JIT align with the principle of least privilege (PoLP)?
JIT aligns with PoLP by ensuring users are granted only the access rights necessary for the specific task at hand, for a limited time, minimizing unnecessary access to sensitive systems or data.
How can JIT access be integrated with existing IAM solutions?
JIT can be integrated through APIs or middleware that communicates between the IAM solution and the resources needing access, automating the provisioning and deprovisioning process based on defined policies.
What are the use cases for JIT access in DevOps environments?
In DevOps, JIT can facilitate seamless access for software updates, configuration changes, or emergency fixes. This ensures developers and operations teams have access only when necessary, enhancing security and operational efficiency.
Does JIT eliminate the need for user accounts and requests altogether?
No, JIT does not eliminate the need for user accounts but rather augments security by providing temporary access. Users still need accounts, but access is dynamically granted and revoked.
What are the security benefits of temporary access compared to standing access?
Temporary access reduces the risk of unauthorized access, data breaches, and potential insider threats by limiting access duration and ensuring users have access only when absolutely necessary.
How does JIT contribute to a zero trust security model?
JIT follows the zero trust principle of “never trust, always verify” by requiring justification for access, ensuring it’s granted temporarily and specifically for each request, aligning with zero trust’s dynamic and context-aware access controls.
How is the duration of access determined in JIT?
The duration is typically determined by policy, the nature of the task, or user request, and can be customized based on the sensitivity of the resources and the minimum time required to complete the task.
What happens when a user’s task takes longer than the initial access period?
The user may request an extension, which undergoes review and approval based on the continued justification for access. This ensures oversight and maintains the principle of least privilege.
How are audit trails and logs managed with JIT access?
JIT solutions automatically log all access requests, approvals, and activities conducted during the access period, providing detailed audit trails for compliance and review.
What security measures are in place to prevent unauthorized access during JIT sessions?
Measures include multifactor authentication (MFA), strict access control policies, real-time monitoring, and automatic session termination upon expiration or anomaly detection.
How are PAM solutions secured against data breaches and privilege elevation attacks?
PAM solutions use encryption, monitoring, anomaly detection, and segregation of duties to protect against breaches and unauthorized privilege escalation, ensuring only authorized users gain access.
Can JIT access be implemented for remote access scenarios?
Yes, JIT can be implemented for remote access to virtual machines, cloud environments, and other resources. This provides secure, temporary access that meets the needs of a distributed workforce.
How do API integrations enable real-time access provisioning with JIT?
API integrations allow JIT systems to communicate in real-time through the aid of IdPs — identity providers — and resource managers.
What are the security considerations for using a central vault for privileged credentials?
Security considerations include robust encryption, access controls to the vault, audit logging of all access to the vault, and secure communication channels for credential retrieval.
How can IT teams leverage automation to manage JIT access workflows efficiently?
IT teams can leverage automation through scripting, orchestration tools, or PAM solution features to streamline the provisioning and deprovisioning of access rights. This includes automatically processing access requests based on predefined policies, executing real-time access grants or revocations, and integrating with existing security systems for immediate response to security incidents.
What are the limitations of JIT access and how can they be addressed?
Limitations of JIT access include potential delays in granting access due to approval processes, complexity in setting up and managing policies, and the challenge of balancing security with user convenience.
All of these can be addressed by optimizing approval workflows, employing AI and machine learning for decision support, and ensuring clear communication and training for all stakeholders to understand the processes and benefits of JIT access.
How does Gartner evaluate different JIT access solutions?
Gartner evaluates JIT access solutions based on criteria such as security features, ease of integration with existing systems, scalability, user experience, and customer support.
How can organizations ensure seamless user adoption and training for JIT access?
Organizations can ensure seamless adoption by providing comprehensive training that explains the benefits and procedures of JIT access, creating user-friendly interfaces and documentation, offering support during the transition, and collecting feedback for continuous improvement.
Can JIT access be used to manage access to sensitive data in addition to privileged accounts?
Yes, JIT access can be extended to manage access to sensitive data, ensuring that users are granted access only when necessary and for a limited time, further protecting the data from unauthorized access and potential breaches.
How can organizations measure the return on investment (ROI) of implementing JIT access?
The ROI can be measured by evaluating the following:
- reduction in security incidents and breaches,
- improved compliance with regulatory requirements,
- increased operational efficiency due to reduced administrative overhead, and
- the overall improvement in the organization’s security posture.
Metrics can include time saved in managing access, reduction in unauthorized access incidents, and cost savings from avoided security incidents.


