Now that Baton, an open source toolkit to extract, normalize, and interact with identity data is available, let’s spend ten minutes installing it and exploring its features. Baton empowers teams to achieve just in time access, least privilege, and is an integral component of access reviews and access management.
Baton launches with prebuilt connectors for AWS, GitHub, MySQL, Okta, and Postgres. We’ll walk through installing the Baton CLI, the Baton GitHub connector, and use them together to show how easy it is to get started with Baton and highlight the value a real time snapshot of SaaS/IaaS platform access privilege is to an organization.
In order to extract, normalize, and interact with identity and access data from any SaaS/IaaS platform, Baton introduces the following data model:
- Resource: A resource is anything in a SaaS/IaaS that can be created, updated, accessed, deleted, audited. In GitHub we have Organizations, Repositories, Teams. In AWS we have Groups, Roles, Accounts. In Okta we have Apps, Groups, Roles. In both MySQL and Postgres we have Columns, Databases, Tables, amongst others.
- Entitlement: An entitlement is a level of access that is grantable on a Resource to a set of other Resource types. For example, in GitHub, a particular Repository Resource may have one or more of the following Entitlements: Admin, Maintain, Pull, Push, Triage.
- Grant: An instance of Entitlement access privilege. As we will see below, a GitHub user with Admin rights to a Repository will be reflected as a Grant in Baton.
We arrive at this data model after building dozens of SaaS/IaaS connectors over the past two years. Some platforms are simple to map while others require more complex features like nested groups or indirect access assigned to groups or roles. We have found success in our simple and extensible data model, which also provides trait annotations for common SaaS/IaaS objects such as Apps, Groups, Roles, Users.
The first step to gain identity access insight into a particular SaaS/IaaS is to write a Baton SDK Connector. The Baton SDK is a framework and toolkit built on the data model above to empower any developer to write and use a Baton Connector to extract identity and access data from any SaaS/IaaS.
Baton launches with 5 Baton Connectors built on the Baton SDK that are ready to use directly, without any programming experience:
Once a Baton Connector exists, we can install it with Homebrew, run it with Docker, or install it from source. Let’s install `baton-github` using Homebrew:
brew install conductorone/baton/baton-github
==> Downloading https://github.com/ConductorOne/baton-github/releases/download/v0.0.8/baton-github-v0.0.8-darwin-arm64.zip
######################################################################## 100.0%
==> Installing baton-github from conductorone/baton
🍺 /opt/homebrew/Cellar/baton-github/0.0.8: 3 files, 27.7MB, built in 2 seconds
Next, create a GitHub Personal Access Token (classic) with repo access:
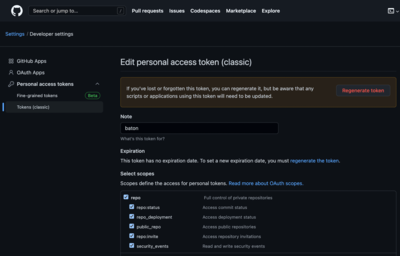
Now either set an environment variable `BATON_TOKEN` to this value, or pass it on the command line to `baton-github`:
BATON_TOKEN=value_from_above BATON_ORGS=c1-test-integration baton-github
{"L":"INFO","T":"2022-12-04T14:18:06.160-0600","C":"zap/grpclogger.go:92","M":"[core][Server #1] Server created","system":"grpc","grpc_log":true}
{"L":"INFO","T":"2022-12-04T14:18:06.160-0600","C":"zap/grpclogger.go:92","M":"[core][Server #1 ListenSocket #2] ListenSocket created","system":"grpc","grpc_log":true}
{"L":"INFO","T":"2022-12-04T14:18:06.164-0600","C":"zap/grpclogger.go:92","M":"[core]CPU time info is unavailable on non-linux environments.","system":"grpc","grpc_log":true}
{"L":"INFO","T":"2022-12-04T14:18:06.570-0600","C":"sync/syncer.go:194","M":"Syncing resource types..."}
{"L":"INFO","T":"2022-12-04T14:18:06.576-0600","C":"sync/syncer.go:262","M":"Syncing resources..."}
{"L":"INFO","T":"2022-12-04T14:18:10.089-0600","C":"sync/syncer.go:411","M":"Syncing entitlements..."}
{"L":"INFO","T":"2022-12-04T14:18:10.115-0600","C":"sync/syncer.go:644","M":"Syncing grants..."}
{"L":"INFO","T":"2022-12-04T14:18:14.116-0600","C":"sync/syncer.go:184","M":"Sync complete."}
Great, we have run our first Baton connector sync, which has extracted and normalized identity and access information from GitHub. The result of the above `baton-github` sync is a file: `sync.c1z`.
In order to view and interact with this information, we use the Baton CLI. Let’s install the Baton CLI via Homebrew:
brew install conductorone/baton/baton
==> Downloading https://github.com/ConductorOne/baton/releases/download/v0.0.9/baton-v0.0.9-darwin-arm64.zip
######################################################################## 100.0%
==> Installing baton from conductorone/baton
🍺 /opt/homebrew/Cellar/baton/0.0.9: 3 files, 26.0MB, built in 2 seconds
Let’s view the Resources that `baton-github` extracted from our sync:
baton resources
ID | Display Name | Resource Type | Parent Resource
96316837 | c1-test-integration | Org | -
111590 | John Degner | User | -
112728839 | lindaparnassus | User | -
6552250 | c1-child-team-1 | Team | c1-parent-team-1 (team)
6552246 | c1-parent-team-1 | Team | c1-test-integration (org)
564630633 | test-repo | Repository | c1-test-integration (org)
As you can see, `baton-github` has provided insight into 1 GitHub Org, 2 GitHub Users, 2 GitHub Teams, and 1 GitHub Repository. We can see who has access privileges by running `baton grants`:
baton grants
Resource Type | Resource | Entitlement | Principal
Repository | test-repo | test-repo Repo Admin | John Degner
Repository | test-repo | test-repo Repo Maintain | John Degner
Repository | test-repo | test-repo Repo Push | John Degner
Repository | test-repo | test-repo Repo Triage | John Degner
Repository | test-repo | test-repo Repo Pull | John Degner
Team | c1-parent-team-1 | c1-parent-team-1 Team Maintainer | John Degner
Team | c1-child-team-1 | c1-child-team-1 Team Maintainer | John Degner
Org | c1-test-integration | c1-test-integration Org Admin | John Degner
Org | c1-test-integration | c1-test-integration Org Member | lindaparnassus
The final Baton CLI capability we will cover today is the `baton diff` command, which will output any changes to identity access privilege state for a SaaS/IaaS since the prior Baton Connector run. First, make an access change to one of your GitHub Resources, we’ll add a user to one of our GitHub repositories:
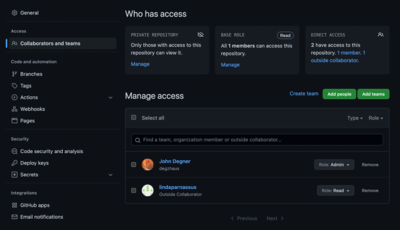
Then, re-run our Baton GitHub connector:
BATON_TOKEN=value_from_above BATON_ORGS=c1-test-integration baton-github
And use the Baton CLI to view the diff:
baton diff
{"resources":{}, "entitlements":{}, "grants":{"created":[{"entitlement":{"resource":{"id":{"resourceType":"repository", "resource":"564630633"}, "parentResourceId":{"resourceType":"org", "resource":"96316837"}, "displayName":"test-repo", "annotations":[{"@type":"type.googleapis.com/c1.connector.v2.ExternalLink", "url":"https://github.com/c1-test-integration/test-repo"}, {"@type":"type.googleapis.com/c1.connector.v2.V1Identifier", "id":"repo:564630633"}]}, "id":"repository:564630633:pull"}, "principal":{"id":{"resourceType":"user", "resource":"112728839"}}, "id":"repository:564630633:pull:user:112728839", "annotations":[{"@type":"type.googleapis.com/c1.connector.v2.V1Identifier", "id":"repo-grant:564630633:112728839:pull"}]}]}}
Pipe `baton diff` to jq for a human readable view, and we see we have added a Grant:
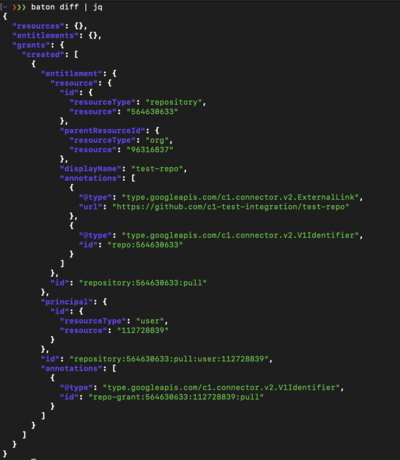
Head over to this tutorial about setting `baton-github` up as a GitHub Action to receive results like these into S3 on an automated schedule. Or jump right into our documentation!
Thanks for reading, please follow us on Twitter or LinkedIn to receive updates on how to achieve least privilege and just in time access and deliver access reviews and access management at your organization.