Compliance audits are a vital part of maintaining a strong security posture and adherence to industry regulations. SOC2 is a compliance audit that ensures you and your service providers securely manage data to protect your organization and clients. The final SOC2 report is a double-sided record that shows both your own security controls (what you have) and how strong they are (what you do).
Choose your adventure
SOC2 audits assess your service providers and security controls against five trust principles:
- Security — Information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise and affect the entity’s ability to achieve its objectives.
- Availability — Information and systems are available for operation and use to meet the entity’s objectives.
- Processing integrity — System processing is complete, valid, accurate, timely, and authorized to meet the entity’s objectives.
- Confidentiality — Information designated as confidential is protected to meet the entity’s objectives.
- Privacy — Personal information is collected, used, retained, disclosed, and disposed of to meet the entity’s objectives.
“You must be this tall to ride.”
Like a rollercoaster height check, these trust principles set a baseline of security practices in an organization: it doesn’t mean instances will not happen, it means you’re up to standard. While there are five (each with differing test criteria), you are only required to choose one. That choice should be guided by your customers’ demands.
Focus on security first
Security is a baseline expectation of vendors; if asked, the majority of your customers would support choosing the security trust principle. For start-ups or first timers, security is usually the best choice. Why? It’s a sales enabler: you can only acquire customers if they trust you to keep them secure. If you’re a B2B company, it’s an implicit prerequisite to sell to other businesses. If you’re in healthcare or finance it’s an operations fundamental given the nature of those businesses’ customers.
Opt for SOC2 Type 2
After you decide on your trust principle, the final decision is whether to do a SOC2 Type 1 or Type 2 audit.
- Type 1 is a point-in-time report
- Type 2 is a period report (repeated every year)
Type 1 is a one-time certification while Type 2 is more sustainable. Most stakeholders expect a Type 2 certification: customers want to know if you are maintaining best practices during the years they are in contract.
We made the decision to pursue a Type 2 report because meeting SOC2 criteria at a single point in time is not enough. Yes, this does mean more work, but we wanted to ensure our internal processes adhere to — or even exceed — best practices for the industry.
You don’t need all five stones
The five trust principles’ test criteria have a lot of overlap, but are different enough that one might not cover all of your customer requirements. That said, it’s uncommon for startups to collect certifications for all five principles. This is usually only seen at large cloud companies like AWS or Cloudflare.
Completing SOC2 certifications is proof that Security, Privacy, or Availability baselines are met. Evidence is only needed for the claims you make.
Before you start: 6 pitfalls to watch out for
Beware of these six common mistakes to avoid complexity, overwork, and headaches:
- Selecting more than one trust principle in your first audit — focus on building a strong workflow, process, and strategy; this is key for smooth sailing during subsequent audits.
- Doing it just to do it — there must be a business reason; your customers and sales team should be telling you SOC2 compliance is important for them.
- Scoping incorrectly — just because a SaaS platform is in scope doesn’t mean it should be; the more controls in scope, the less centralized the data, and the more complicated your security and remediation can be.
- Going it alone — starting from scratch used to be the norm. Today, there are templates, tools, and automations to help you on your journey.
- Timing it poorly — your first Type 2 often has a three-month monitoring period; take into consideration any planned time off, launches, or code freezes before starting.
- Putting it off — complexity increases with maturity. A steady state of compliance is easier to maintain and optimize once the standard has been set.
A seventh mistake could be not going through the below readiness assessment prior to completing a SOC2 examination for the first time. Read the five steps below to understand what it takes to get ready for a security audit.
Steps to SOC2 Compliance
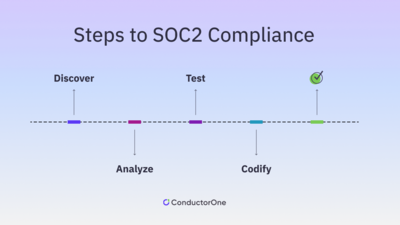
Step 1
Discover: data and definitions
Map a comprehensive list of your corporate digital assets to gain a true scope that you and your teammates (and eventually an auditor) can work with. What resources have data? Collaborate with other teams on what types there are, what documenting looks like, how it is defined, and where it is stored. If you outsource a SaaS software, this includes assessing your vendor security controls.
“The best data is data you don’t have”
Companies are adopting the principle of data minimization: if your controls don’t need it, don’t have it. During scoping, that means changing the data definitions in SaaS or other controls. In practice, that looks like using customer IDs instead of email addresses as unique identifiers in an analytics platform; the app no longer holds PII, taking it out of scope. The audit is now easier, the data sprawl is lessened, and everyone is more secure.
Step 2
Analyze: people and processes
Now that you know your data landscape, doing a gap analysis will show where security objectives and best practices are met, and, if not, what steps — process improvements and security projects — should be taken.
Non-security teams don’t necessarily think about data protection as the top priority for the applications and resources they own. Data security can be compromised unintentionally and neglecting to enable those owners and their systems with security controls can expose them to risk.
Step 3
Test: systems and software
Once you’ve noted areas for personnel improvements with a gap analysis, conducting an access review will reveal potential system improvements. Access reviews are designed to uncover issues like overprivilege, mistakes or changes in user roles, or inappropriate access, all of which can introduce vulnerabilities. Understand where your systems’ limits are to find risk areas:
- Test network functionality and file integrity
- Document and disclose security incidents
- Track user access
- Install MFA or SSO
- Get risk analysis in context
Distribute access controls and enable the owners of those systems. Usually, a security vulnerability lies where basic security systems should be, but aren’t.
Step 4
Codify: policies and productivity
Determine data classification, handling, and access, then write policies that hardcode those rules into your organization’s operations. A few teams will be involved, especially when creating new policies. Security’s lens ensures technical feasibility and that policy changes don’t unintentionally introduce security risks, while the IT lens vies for productive employee experiences. If you deem all data/access as critical, you end up making life difficult for IT and stakeholders. If you deem all data/access as available to everyone, you end up with unnecessary vulnerabilities.
Review existing policies for clarity and make updates as needed to ensure they are still relevant. Codify unwritten processes — for example, informal steps that have been adopted over time to keep customer data secure — into formal security policies.
The best data classification and security policies are designed for both business productivity and security.
Policy Pro-Tip
Writing new policies from scratch can be a multiple-month process. Search for policy templates online and adapt them to your needs. Companies like Vanta or Drata have tools and guidance for this.
Adapting templates to your unique company infrastructure is the key to success because your auditor will grade you according to what is in them, applicable or not. Your policies will drive your security roadmap and help you determine where to build in productivity and where to make investments in automation.
Step 5
Clean
Fix as many issues as you can before the auditor begins their assessment — this will make for a less redundant report — and allow you to get your security strategy off the ground before the final report.
Conclusion
Using this readiness checklist will get you in solid shape for a SOC2 audit while going beyond audit readiness. A proactive, comprehensive security strategy can establish trust, drive revenue, and unlock new business for your organization as much as it can prevent fines and damages resulting from noncompliance and exposed data.
To sum it all up:
- Identify high-risk control gaps
- Improve process, policies, and systems
- Remediate issues prior to the official SOC2 audit
- Plan for the future
SOC2 is continuous. Once you finish, you’re in the next audit period, so you should foster a security mindset that is always on, repeatable, and scalable.
Everyone is at a different point on their compliance journey, so reach out and chat with us if you want to learn more or looking for further guidance. If you’re ready to get started, we’ve got tools to help you create this foundation — check out our access review toolkit here or head to the solutions page for more information.