What’s better than a zero trust VPN replacement that gives employees remote access to private resources and networks? Being able to manage that access with the principle of least privilege and automation. Enter Twingate + ConductorOne, a match made in integration heaven.
While our list of integrations has more than doubled over the last few months, Twingate is worth mentioning in the context of building Zero Trust architectures.
Who is Twingate?
Twingate makes it easy to adopt and maintain a Zero Trust networking model by mapping resources on your network, assigning approved users, and connecting from any device, anywhere. Users love Twingate because it quietly runs in the background and creates direct secure access to your office network, cloud VPCs, backend and production infrastructure, and other private corporate resources with no impact on user performance or latency. Their smart routing network engine combines modern technologies like NAT traversal, QUIC, private proxies, and split tunneling to give users a fast and secure connection. They provide lightweight integrations that connect to any cloud or on-prem infrastructure, creating quick time to value.
The ConductorOne + Twingate Impact on Security
With Twingate, you can define fine-grain access policies based on user, location, and device. That enables companies to enforce device restrictions and posture checking for access to corporate resources and infrastructure which can contain sensitive data and are at higher-risk for data breaches when access is left unchecked.
ConductorOne takes this a step further by layering on least privilege access controls. Instead of granting standing privileges to those critical resources, ConductorOne provides the automation and orchestration for just-in-time and time-bound access. With a no-code approval workflow builder, you can customize the approver, chain of command, reassignment, and self-review options for access requests. Employees can self-serve requests from a customizable catalog in a web app or directly through common collaboration tools like Slack. Upon approval, ConductorOne takes care of the provisioning, and if the access granted has a limited time period, ConductorOne will automatically deprovision access at the expiration.
Moving to just-in-time access reduces standing privileges and helps security teams get one step closer to Zero Trust. And for IT teams, self-service access requests means no more triaging a myriad of access requests tickets, chasing down managers, or manually provisioning access. Plus, the ConductorOne + Twingate integration gives you visibility into all local, SSO, or federated users that have access to Twingate resources, all from one single pane of glass that makes it easy to scope and automate user access reviews.
How It Works
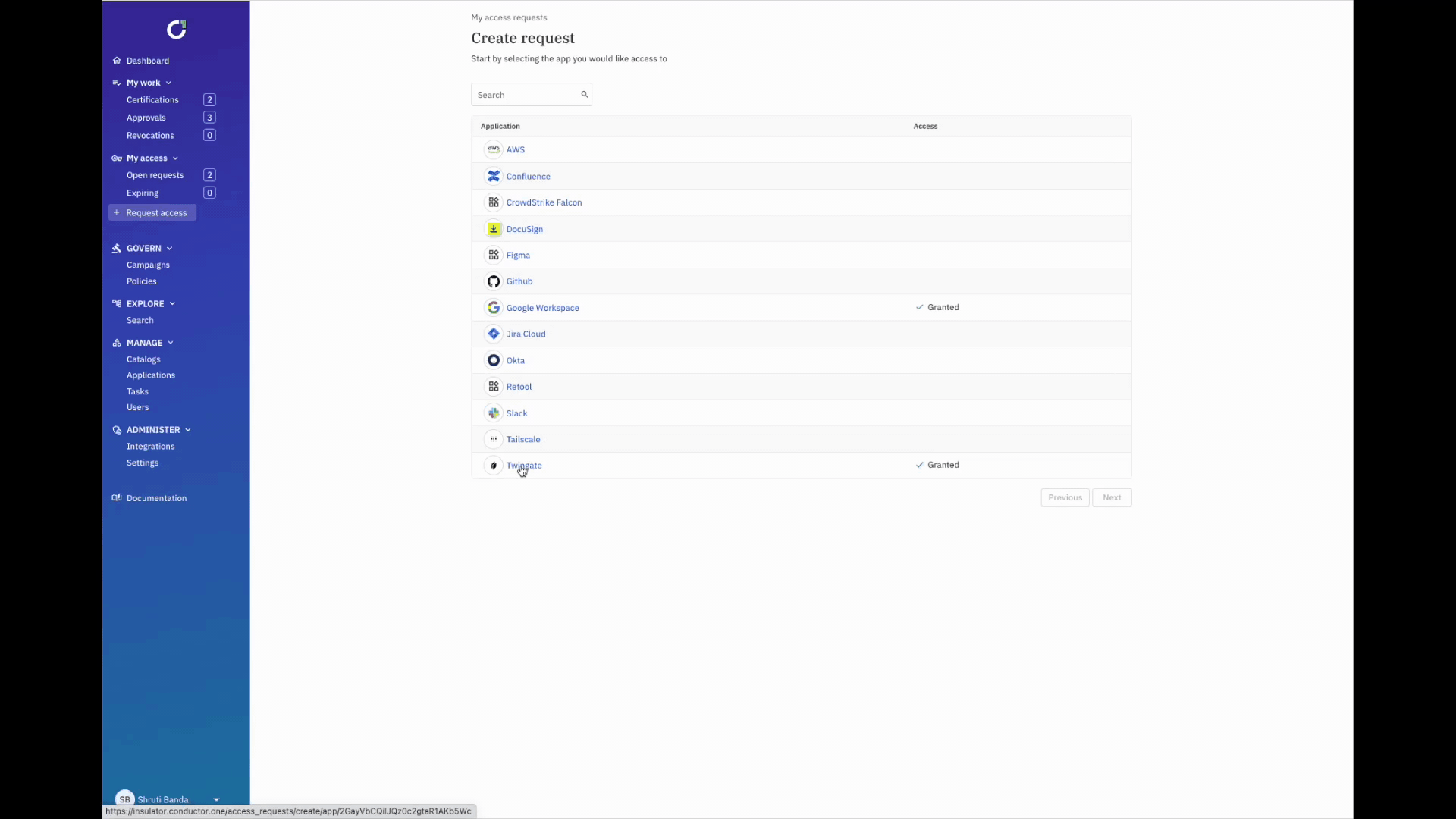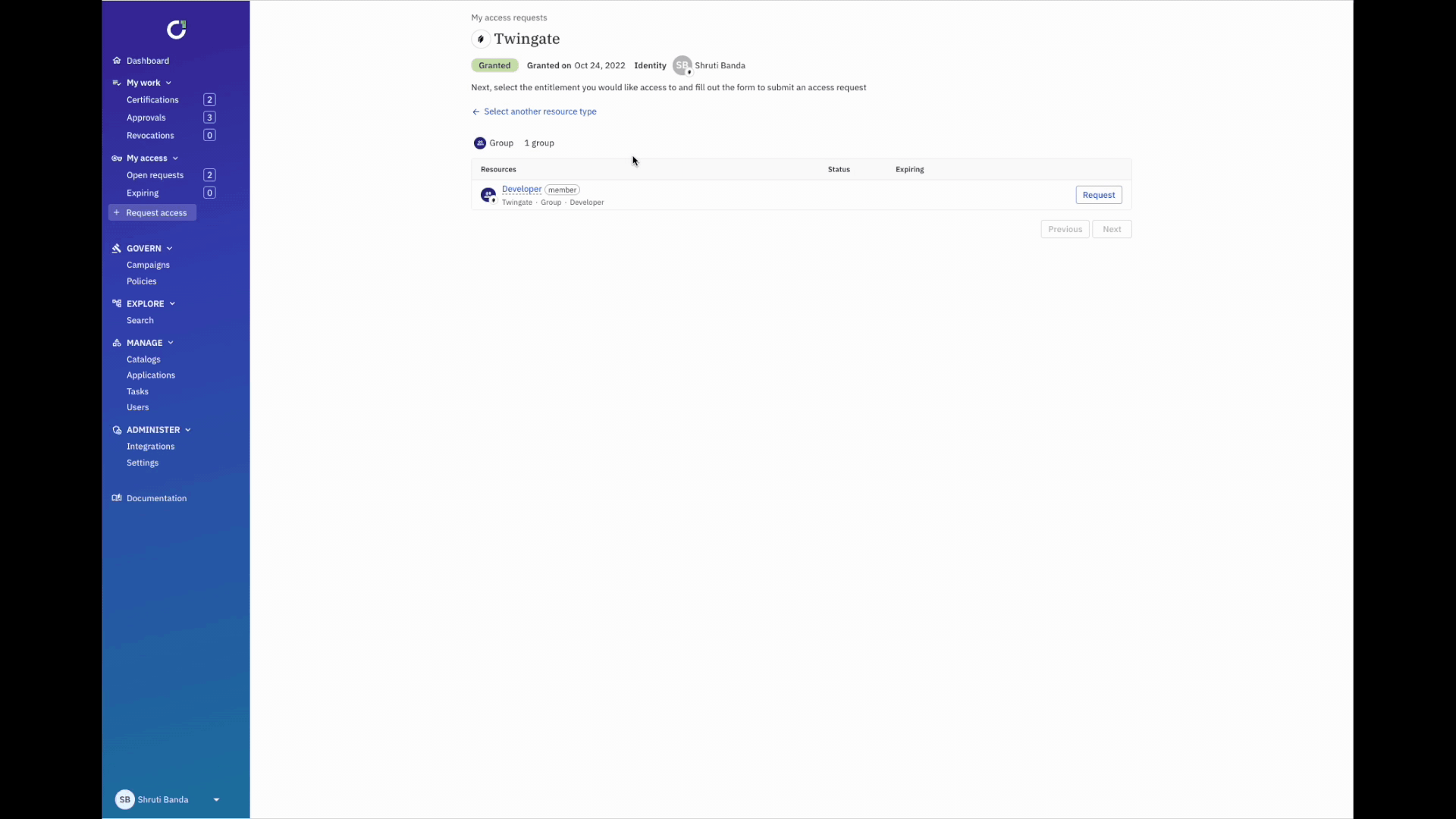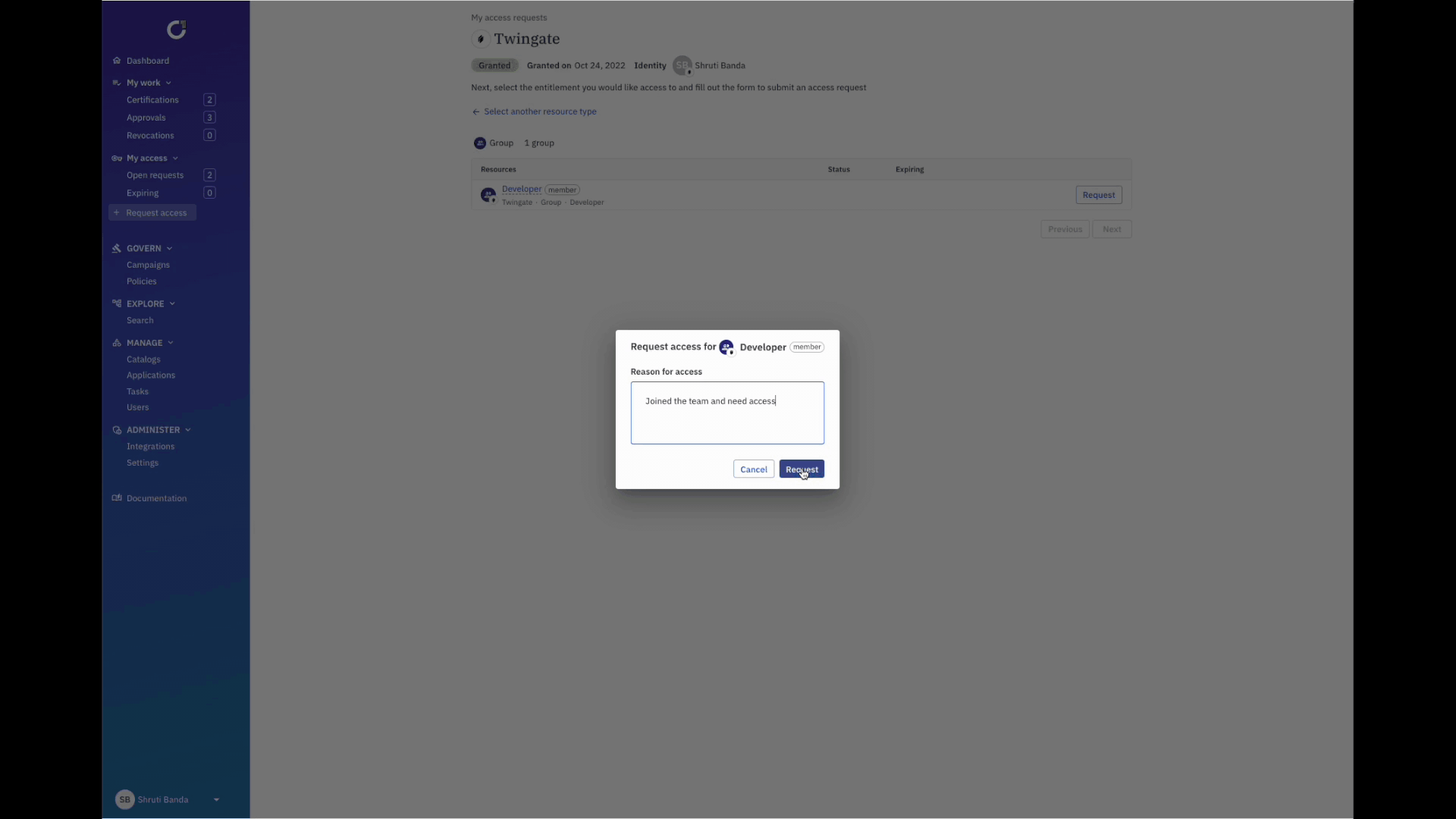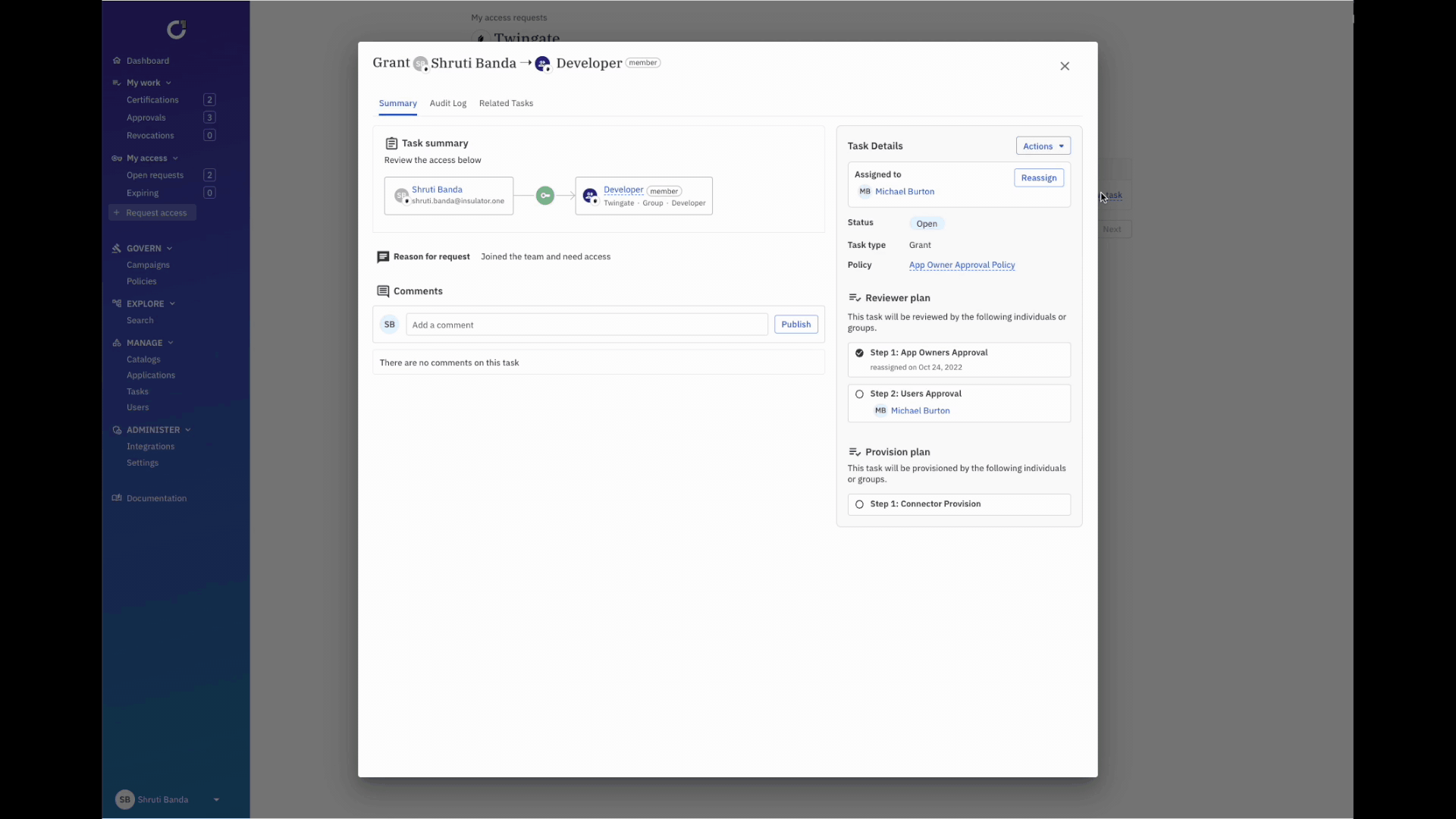
- Using ConductorOne, users request access to a particular resource in Twingate via Slack or web.
- Customized approval workflows based on the chain of command, length of time, and more, are triggered.
- Reviewers can approve or deny directly in Slack, and users are automatically provisioned.
- ConductorOne automatically revokes access and deprovisions users after a set period of time.
Our goal at ConductorOne is to help companies become more secure without the pain of extra manual work. Now with Twingate, architecting a Zero Trust solution with just-in-time, secure connection to private resources became a lot easier. Learn more about the Twingate + ConductorOne integration here.
We’re just getting started and we’d love to have you join us on the journey!